Zilliz Cloud BYOC Upgrades: Bring Enterprise-Grade Security, Networking Isolation, and More

As organizations move AI search applications from prototypes to production, they face a critical infrastructure challenge: how to deploy vector databases while maintaining strict security and compliance requirements. According to McKinsey's 2024 survey, while 72% of organizations are now using AI, nearly half of healthcare organizations still restrict AI adoption due to data privacy concerns. The core issue isn't the AI technology itself - it's the infrastructure needed to deploy it securely at scale.
This release of Zilliz Cloud BYOC addresses these deployment challenges with new security features and enhanced operational capabilities. Organizations can now run vector search infrastructure in their cloud environment with improved control over their data and operations.
The Enterprise AI Infrastructure Dilemma
Organizations implementing AI at scale face a critical challenge that often plays out in boardrooms across regulated industries: While AI pilots demonstrate impressive results - like 40% improvements in customer service response times - moving from prototype to production isn't just about scaling up. It requires navigating a complex maze of security requirements, compliance regulations, and operational constraints.
Traditional approaches each create significant tradeoffs:
Public SaaS Solutions: While offering robust out-of-the-box capabilities, they require data to reside in vendor cloud accounts and communications over public networks - often a non-starter for regulated industries.
On-premise Deployments: While providing complete control, they demand significant investment in dedicated DevOps teams and create operational overhead that can become overwhelming as AI technology evolves.
BYOC Architecture: Security by Design
The BYOC architecture implements a dual-plane design that ensures complete data sovereignty while providing the convenience of a managed service. At its core, the control plane serves as the management layer, handling critical operational tasks without ever accessing customer data. It orchestrates resource scheduling, system upgrades, and infrastructure provisioning through secure, encrypted connections with strictly controlled access policies and dedicated communication channels. This architecture enables automated management while maintaining strict access controls—any troubleshooting access by Zilliz engineers requires explicit customer consent and follows a rigorous security protocol.
The data plane, running entirely within the customer's VPC, manages all data operations with complete isolation. Every vector search, query process, and index management operation occurs within your network boundaries. All data and metadata are securely contained within your VPC, with communications protected by TLS encryption.
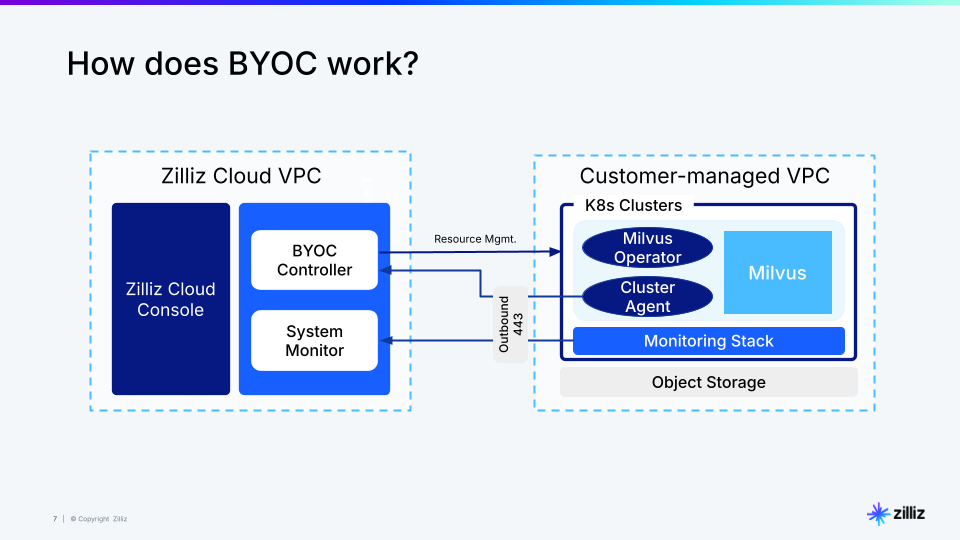
Building on this secure foundation, this release introduces a set of new features that enhance both security and operational capabilities:
Fine-Grained Permission Control
This release introduces a comprehensive permissions management system that implements true least-privilege access through sophisticated IAM integrations. At its foundation is a new storage role permission set that enables fine-grained control over S3 operations, from bucket listing to object retrieval and data modifications. Each operation is explicitly defined and controlled, ensuring data access follows strict security protocols.
The system extends beyond basic storage controls, including detailed EKS role management capabilities. It incorporates AWS-managed permissions for EC2 container registry access, VPC resource control, and cluster policies while integrating with Kubernetes SIGs permissions for load balancer control, EBS storage management, and cluster auto-scaling.
A particularly powerful addition is the new cross-account role framework, which enables precise control over cluster creation, node group management, and resource tagging. Organizations can now manage permissions across multiple levels—organization, project, and cluster—with each permission carefully scoped to specific resources and operations. This granular approach ensures teams can operate efficiently while maintaining strict security boundaries.
Comprehensive Audit Logging
The new audit logging system transforms operational visibility by capturing every interaction within the data plane. Every search query, index creation, and data modification is recorded with complete execution context, including query parameters, performance metrics, and resource utilization. The system extends beyond database operations to track all configuration changes, scaling operations, and infrastructure updates, capturing detailed before-and-after states. Additionally, every authentication attempt, permission check, and resource access is recorded with full user context and access patterns.
Logs are automatically streamed to your designated storage bucket with a structured organization:
Structured file paths:
/<Cluster ID>/<Log type>/<Date>Standardized naming:
HH:MM:SS-$UUID
This structured approach simplifies security reviews, compliance audits, and operational troubleshooting. Integration with AWS CloudWatch provides additional monitoring and analysis capabilities.
Enhanced Network Security
This release introduces complete network isolation through AWS PrivateLink integration. Organizations can now establish private endpoints within their application VPCs for secure cluster access, eliminating public internet exposure for all vector search operations. The service is available in us-west-2 and eu-central-1 regions, with seamless integration into existing VPC security groups and network ACLs. Organizations maintain full control through customer-managed endpoints and security policies.
The communication security model has also been significantly enhanced. All system communications now operate exclusively through outbound port 443, with TLS 1.2+ encryption and support for custom certificate management. A new WAF-enabled Network Load Balancer provides advanced threat detection and blocking capabilities, along with custom rule sets for access control and DDoS protection. Enhanced private link support ensures dedicated connection paths for control plane traffic, with isolated routing policies and granular network monitoring.
Infrastructure Automation
This release includes comprehensive infrastructure-as-code support through both AWS CloudFormation and Terraform to streamline deployments. The CloudFormation templates provide complete BYOC infrastructure provisioning, with pre-configured security groups, network settings, and automated EKS cluster setup following security best practices. The templates support custom parameters for environment-specific configurations and natively integrate with existing VPC resources.
For teams using Terraform, we've developed modular deployment scripts that handle everything from S3 bucket creation with proper encryption and access policies to IAM role configuration with least-privilege permission sets. The scripts implement state management best practices and support multiple environment deployments with custom variable templates to meet enterprise requirements.
Looking Ahead: Multi-Cloud Support
While this release focuses on AWS capabilities, we're actively developing support for other major cloud providers. Google Cloud Platform support is now available as a private preview, with Azure on our near-term roadmap. This expansion will enable true multi-cloud deployment flexibility, meeting the diverse needs of enterprise customers across different cloud environments.
Zilliz Cloud BYOC is currently generally available on AWS. Organizations interested in deploying vector search infrastructure with enterprise-grade security and control can contact our team to learn more about implementation options and requirements.
The upgraded Zilliz Cloud BYOC represents a significant step forward in enterprise AI infrastructure, enabling organizations to deploy production-ready vector search capabilities while maintaining stringent security and compliance standards. As AI continues to transform enterprise operations, solutions like BYOC will be essential for organizations striving to balance innovation with security and control.
- The Enterprise AI Infrastructure Dilemma
- BYOC Architecture: Security by Design
- Looking Ahead: Multi-Cloud Support
Content
Start Free, Scale Easily
Try the fully-managed vector database built for your GenAI applications.
Try Zilliz Cloud for FreeKeep Reading
Why and How to Migrate from Self-Hosted Milvus to Zilliz Cloud
A simple, step-by-step guide to migrating from Milvus to Zilliz Cloud. Learn both endpoint and backup methods for a smooth, scalable vector database migration.

Building RAG Pipelines for Real-Time Data with Cloudera and Milvus
explore how Cloudera can be integrated with Milvus to effectively implement some of the key functionalities of RAG pipelines.

How to Calculate the Total Cost of Your RAG-Based Solutions
In this guide, we’ll break down the main components of RAG costs, show you how to calculate these expenses using the Zilliz RAG Cost Calculator, and explore strategies to manage spending efficiently.
