How Zilliz Cloud Protects Your Data

Moving vector search workloads to the cloud require a well-thought-out strategy, including a complex combination of managing your data's safety and availability. One key point to keep in mind is data protection. Data protection is significant since your data is valuable, and losing it can have catastrophic consequences. Additionally, security is another crucial aspect to consider. The cloud can be a safe place to store your data, but it is vital to take precautions to prevent unauthorized access. Finally, high availability is also an essential factor to consider. You want to make sure that your data is always accessible, even in the event of a service failure.
Three Pillars of Infosec - Confidentiality, Integrity and Availability
Regarding security incidents, many people's first reaction is token leakage, database deletion by mistake, and other accidents, but the scope of security is far more than that. Information security includes confidentiality, integrity, and availability. Among them, confidentiality refers to protecting data from unauthorized access or disclosure, the most well-known security incident; integrity refers to protecting data from tampering or destruction. Integrity incidents often are not caused by external attackers but by improper operation and script bugs within the company; availability refers to ensuring that data is available when needed. These three elements are the foundation of the information security system.
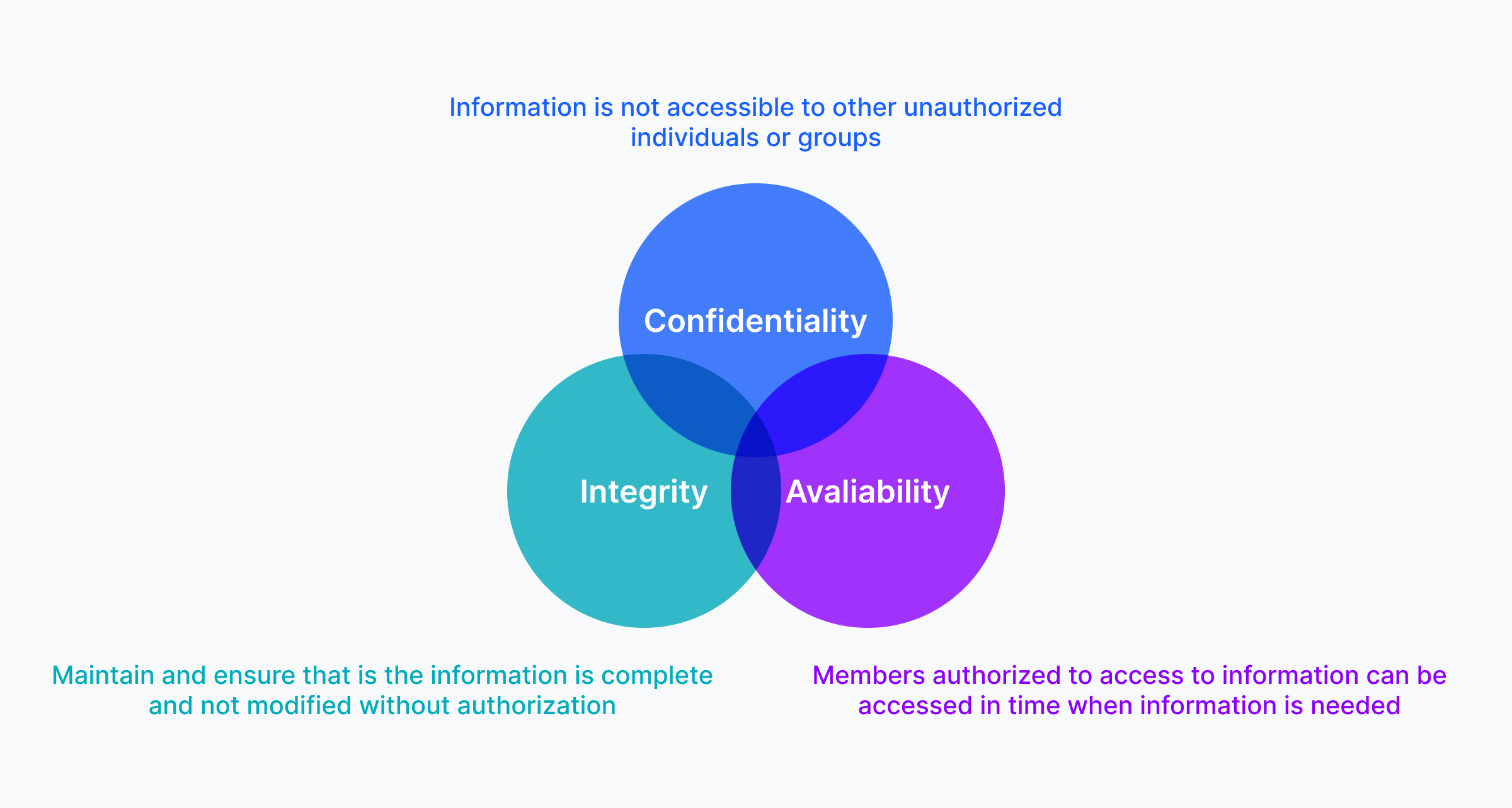 Three Pillars of Infosec: Confidentiality, Integrity and Availability
Three Pillars of Infosec: Confidentiality, Integrity and Availability
10 Common Data Management Mistakes
By staying alert and taking proactive measures, you can significantly reduce the risk of data loss. Here are ten common data management mistakes.
- DevOps or DataOps mistakes
- Skipping rigorous testing procedures and going straight to production
- Lack of rigorous data management (deletion, update) approval procedures
- Lack of backups and data recovery
- Unprotected network access
- Running out-of-date executables without the latest security patches
- Failure to control privileged access
- Weak passwords, improper key management
- Dependency on third-party services with poor availability
- Dependence on a single datacenter or cloud provider
Points 1 through 4 above form the four primary data management failsafes. Effective data management in production environments involves three crucial layers of protection. Firstly, mistakes made by DevOps teams, which can lead to accidental data deletion, must be mitigated by implementing strict controls over scripts and conducting sanity checks before execution. Second, any action taken must first be throughly tested in a sandboxed development environment. Third, a lack of rigorous data management procedures and compliance can be addressed by creating standard procedures for data management and compliance, and ensuring that checks are conducted by different teams before customer data residing in production is manipulated. Lastly, automated sanity checks and regular backups should be implemented before any action (such as data deletion) is taken to verify data integrity and prevent permanent loss. By addressing these three layers of data management and security, organizations can reduce the risk of data loss or compromise in production environments.
With the rapid advancement of AI technology, the importance of unstructured data for businesses is steadily increasing. As companies accumulate data, they explore new ways to leverage unstructured data to enhance product experience. Therefore, data security, integrity, and availability have become increasingly important topics as the volume and value of data continue to grow. As a critical component of unstructured data retrieval, a vector database must provide the powerful capability to keep your data safe and sound.
How Zilliz Cloud Protects Your Data and Services
For these reasons, Zilliz Cloud offers a range of features to help you confidently manage your data. With Zilliz Cloud, you can be assured that your data is secure, highly available, and will never be lost. Zilliz Cloud has completed SOC2 Type 2 certification at the fastest speed and actively meets other certifications to ensure the highest level of security and compliance.
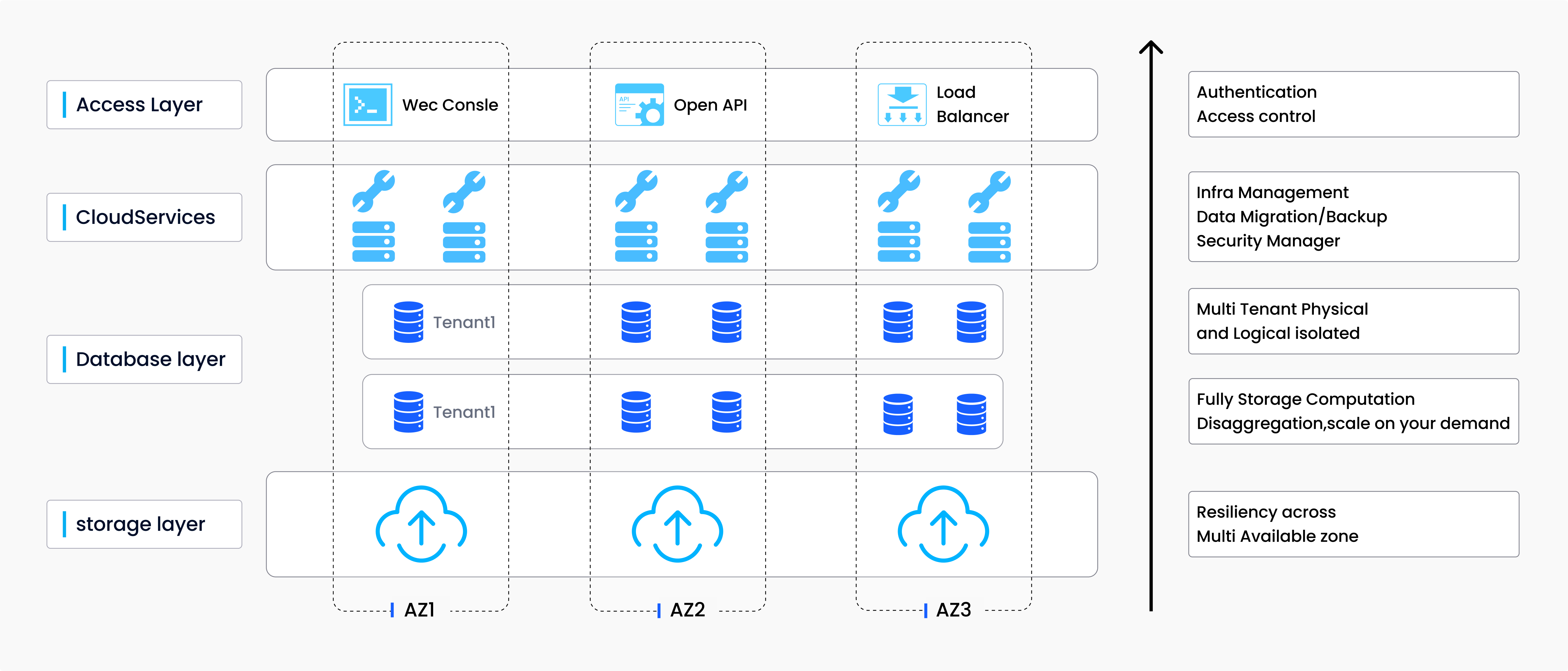 Zilliz Cloud architecture.
Zilliz Cloud architecture.
Confidentiality: Zilliz Cloud employs a multi-layered security approach, including security standards prohibiting access to user data. TLS encrypts data sent to and from your vector database, while RBAC, Audit logs, ALB IP Whitelisting, Privatelink, Auth0, AWS Secrets Manager, and IAM provide various security and permission management features for protecting private and sensitive information, controlling user access, tracking object changes, securing traffic, and encrypting passwords. All of these work in tandem to ensure that you and only you have access to your data.
Integrity: We provide various data management services to ensure the safety and accessibility of your data. These services include data backups, which allow you to back up your collection to S3 and recover to another collection in the event of accidental deletion or data corruption. We also offer a data recovery bin that retains data for a certain period after operations such as table deletion and cluster release, to avoid unintended deletion or manipulation. Furthermore, we are currently developing change data capture, which will enable incremental data subscriptions, allowing you to archive data to data warehouses or object storage that you write into Zilliz cloud.
Availability: Zilliz Cloud offers physical isolation via resource groups and multi-tenancy features along with a 99.9% SLA. Resource groups and multi-tenancy allow for the isolation of multi-tenant data and services to safeguard your data against accidental or intentional deletion. As a result, Zilliz cloud provides an even higher degree of data protection and service resilience compared to offline deployment. Upon ingestion, data is synchronously and transparently replicated across three availability zones.
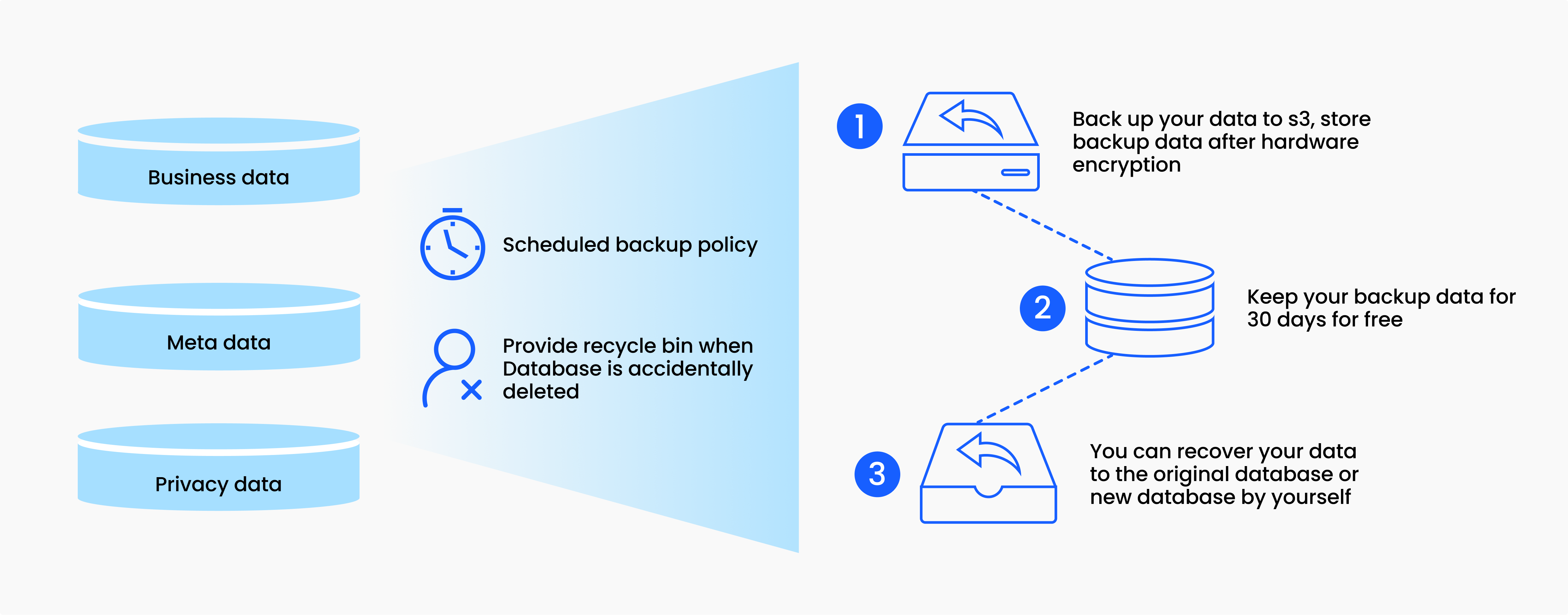 How Zilliz Cloud protects your data and services
How Zilliz Cloud protects your data and services
Summary
Here at Zilliz, we take data security very seriously. A single breach or accidental deletion can cause significant financial losses for individuals and companies. Our vector-search-as-a-service takes care of the nitty-gritty for you. At Zilliz Cloud, we remain committed to data and strive to provide our users with the world's most secure and reliable cloud vector database service. To learn more about our security approach, check out the Zilliz security page.
- Three Pillars of Infosec - Confidentiality, Integrity and Availability
- 10 Common Data Management Mistakes
- How Zilliz Cloud Protects Your Data and Services
- Summary
Content
Start Free, Scale Easily
Try the fully-managed vector database built for your GenAI applications.
Try Zilliz Cloud for FreeKeep Reading

Balancing Precision and Performance: How Zilliz Cloud's New Parameters Help You Optimize Vector Search
Optimize vector search with Zilliz Cloud’s level and recall features to tune accuracy, balance performance, and power AI applications.

Knowledge Injection in LLMs: Fine-Tuning and RAG
Explore knowledge injection techniques like fine-tuning and RAG. Compare their effectiveness in improving accuracy, knowledge retention, and task performance.
Vector Databases vs. In-Memory Databases
Use a vector database for AI-powered similarity search; use an in-memory database for ultra-low latency and high-throughput data access.
